Itã¢â‚¬â„¢s Easy to Envision an Algorithm That Recognizes the Self Without Being Aware of the Self

Face up Recognition: Understanding LBPH Algorithm
Human beings perform confront recognition automatically every day and practically with no try.
Although it sounds like a very simple task for united states of america, it has proven to be a complex task for a computer, as it has many variables that tin impair the accuracy of the methods, for example: illumination variation, low resolution, occlusion, amongst other.
In informatics, face recognition is basically the chore of recognizing a person based on its facial paradigm. It has become very popular in the last two decades, mainly because of the new methods developed and the high quality of the current videos/cameras.
Note that face recognition is different of face detection:
- Face Detection: it has the objective of finding the faces (location and size) in an image and probably extract them to be used by the face recognition algorithm.
- Face Recognition: with the facial images already extracted, cropped, resized and usually converted to grayscale, the face recognition algorithm is responsible for finding characteristics which best describe the image.
The face recognition systems can operate basically in two modes:
- Verification or hallmark of a facial image: it basically compares the input facial image with the facial image related to the user which is requiring the authentication. Information technology is basically a 1x1 comparing.
- Identification or facial recognition: it basically compares the input facial image with all facial images from a dataset with the aim to notice the user that matches that face. It is basically a 1xN comparing.
There are different types of face up recognition algorithms, for example:
- Eigenfaces (1991)
- Local Binary Patterns Histograms (LBPH) (1996)
- Fisherfaces (1997)
- Calibration Invariant Characteristic Transform (SIFT) (1999)
- Speed Upwards Robust Features (SURF) (2006)
Each method has a different arroyo to extract the paradigm information and perform the matching with the input epitome. However, the methods Eigenfaces and Fisherfaces have a similar approach as well as the SIFT and SURF methods.
Today nosotros gonna talk nearly one of the oldest (not the oldest one) and more popular face recognition algorithms: Local Binary Patterns Histograms (LBPH).
Objective
The objective of this post is to explain the LBPH as simple every bit possible, showing the method stride-by-footstep.
As it is one of the easier face recognition algorithms I think anybody can empathize information technology without major difficulties.
Introduction
Local Binary Pattern (LBP) is a simple yet very efficient texture operator which labels the pixels of an image by thresholding the neighborhood of each pixel and considers the event as a binary number.
Information technology was first described in 1994 (LBP) and has since been constitute to be a powerful feature for texture classification. Information technology has further been determined that when LBP is combined with histograms of oriented gradients (HOG) descriptor, information technology improves the detection operation considerably on some datasets.
Using the LBP combined with histograms nosotros can stand for the face images with a simple data vector.
As LBP is a visual descriptor it can as well be used for face recognition tasks, as can be seen in the following step-past-step explanation.
Note: you can read more nearly the LBPH here: http://www.scholarpedia.org/article/Local_Binary_Patterns
Step-past-Step
At present that we know a picayune more most face recognition and the LBPH, let's get further and come across the steps of the algorithm:
- Parameters: the LBPH uses 4 parameters:
- Radius: the radius is used to build the circular local binary pattern and represents the radius effectually the cardinal pixel. It is normally set up to one.
- Neighbors: the number of sample points to build the round local binary blueprint. Keep in listen: the more sample points y'all include, the higher the computational price. It is usually set up to 8.
- Grid X: the number of cells in the horizontal direction. The more than cells, the finer the grid, the higher the dimensionality of the resulting feature vector. Information technology is commonly prepare to eight.
- Grid Y: the number of cells in the vertical direction. The more cells, the finer the grid, the higher the dimensionality of the resulting feature vector. Information technology is usually set to viii.
Don't worry well-nigh the parameters right now, you volition sympathise them later reading the next steps.
2. Grooming the Algorithm: First, we need to train the algorithm. To do so, nosotros need to utilise a dataset with the facial images of the people we desire to recognize. We need to as well prepare an ID (it may be a number or the proper name of the person) for each prototype, so the algorithm volition use this information to recognize an input epitome and give you an output. Images of the same person must take the same ID. With the training set already synthetic, let's run across the LBPH computational steps.
three. Applying the LBP operation: The outset computational pace of the LBPH is to create an intermediate image that describes the original epitome in a meliorate way, by highlighting the facial characteristics. To do so, the algorithm uses a concept of a sliding window, based on the parameters radius and neighbors.
The epitome beneath shows this process:

Based on the epitome above, let's pause information technology into several small steps so nosotros tin empathise it easily:
- Suppose nosotros have a facial image in grayscale.
- Nosotros tin can get part of this paradigm as a window of 3x3 pixels.
- It can besides be represented equally a 3x3 matrix containing the intensity of each pixel (0~255).
- Then, we need to have the central value of the matrix to be used every bit the threshold.
- This value will exist used to define the new values from the 8 neighbors.
- For each neighbour of the central value (threshold), we ready a new binary value. We fix i for values equal or college than the threshold and 0 for values lower than the threshold.
- At present, the matrix volition contain only binary values (ignoring the central value). Nosotros demand to concatenate each binary value from each position from the matrix line by line into a new binary value (e.yard. 10001101). Notation: some authors use other approaches to concatenate the binary values (eastward.g. clockwise management), but the terminal result volition be the aforementioned.
- Then, we convert this binary value to a decimal value and gear up information technology to the fundamental value of the matrix, which is actually a pixel from the original prototype.
- At the terminate of this process (LBP process), we have a new epitome which represents meliorate the characteristics of the original epitome.
- Note: The LBP procedure was expanded to use a different number of radius and neighbors, it is called Circular LBP.

Information technology can be done past using bilinear interpolation. If some data point is between the pixels, it uses the values from the 4 nearest pixels (2x2) to estimate the value of the new data signal.
4. Extracting the Histograms: Now, using the image generated in the last step, we can use the Grid 10 and Grid Y parameters to divide the epitome into multiple grids, as tin can be seen in the following image:

Based on the image above, we tin can extract the histogram of each region as follows:
- As we have an image in grayscale, each histogram (from each grid) will contain only 256 positions (0~255) representing the occurrences of each pixel intensity.
- And then, we need to concatenate each histogram to create a new and bigger histogram. Supposing we take 8x8 grids, we will take 8x8x256=xvi.384 positions in the final histogram. The final histogram represents the characteristics of the image original image.
The LBPH algorithm is pretty much it.
5. Performing the confront recognition: In this step, the algorithm is already trained. Each histogram created is used to represent each image from the grooming dataset. Then, given an input image, we perform the steps again for this new prototype and creates a histogram which represents the image.
- Then to discover the prototype that matches the input prototype we merely demand to compare two histograms and render the image with the closest histogram.
- We can use various approaches to compare the histograms (summate the altitude between two histograms), for example: euclidean distance, chi-square, accented value, etc. In this example, nosotros can use the Euclidean distance (which is quite known) based on the post-obit formula:
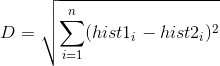
- So the algorithm output is the ID from the epitome with the closest histogram. The algorithm should also return the calculated distance, which can be used every bit a 'conviction' measurement. Notation: don't be fooled nearly the 'confidence' name, as lower confidences are better considering it means the distance betwixt the two histograms is closer.
- We can then use a threshold and the 'confidence' to automatically estimate if the algorithm has correctly recognized the image. We can assume that the algorithm has successfully recognized if the confidence is lower than the threshold defined.
Conclusions
- LBPH is one of the easiest face recognition algorithms.
- It can correspond local features in the images.
- Information technology is possible to go great results (mainly in a controlled environment).
- It is robust against monotonic greyness scale transformations.
- Information technology is provided by the OpenCV library (Open Source Estimator Vision Library).
LBPH algorithm
I am implementing the LBPH algorithm in Go programming language. The projection is available on Github and is distributed under the MIT license, so feel costless to contribute to the project (whatsoever contributions are welcome).
Link to the project: https://github.com/kelvins/lbph
Note: as mentioned in the conclusions, the LBPH is also provided by the OpenCV library. The OpenCV library can exist used by many programming languages (e.thousand. C++, Python, Ruby, Matlab).
If you lot liked this story please requite information technology a clap. Information technology motivates me to write more stories most confront recognition.
References
- Ahonen, Timo, Abdenour Hadid, and Matti Pietikainen. "Face description with local binary patterns: Application to face up recognition." IEEE transactions on design assay and machine intelligence 28.12 (2006): 2037–2041.
- Ojala, Timo, Matti Pietikainen, and Topi Maenpaa. "Multiresolution greyness-scale and rotation invariant texture classification with local binary patterns." IEEE Transactions on design analysis and motorcar intelligence 24.7 (2002): 971–987.
- Ahonen, Timo, Abdenour Hadid, and Matti Pietikäinen. "Face recognition with local binary patterns." Computer vision-eccv 2004 (2004): 469–481.
- LBPH OpenCV: https://docs.opencv.org/2.4/modules/contrib/dr./facerec/facerec_tutorial.html#local-binary-patterns-histograms
- Local Binary Patterns: http://world wide web.scholarpedia.org/article/Local_Binary_Patterns
Source: https://towardsdatascience.com/face-recognition-how-lbph-works-90ec258c3d6b
Post a Comment for "Itã¢â‚¬â„¢s Easy to Envision an Algorithm That Recognizes the Self Without Being Aware of the Self"